Microsoft Entra ID for BrowZer
Get an Entra ID Account
If you don't already have an account you can sign up at https://entra.microsoft.com/
Add a new Application
Once you have an Azure account, click on the "Entra" icon in the navbar:
Then click on the "App Registrations" item in the left navbar:
Then Click "New registration":
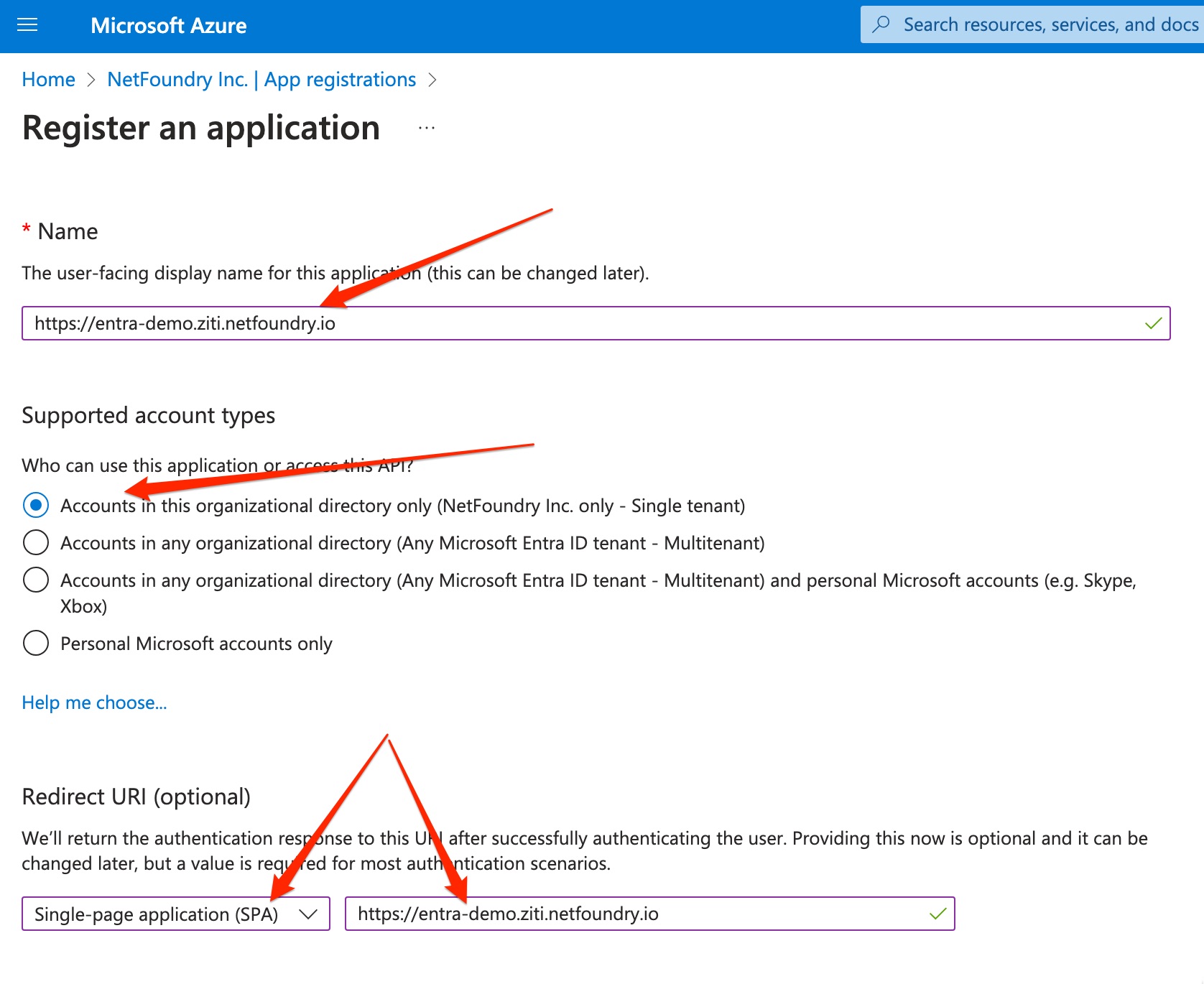
Now Register an Application:
For the Name of the application, enter the URL where you will be hosting your browZer bootstrapper. For the example used in this documentation, we will use https://entra-demo.ziti.netfoundry.io
For the Supported account types, click the top option (single tenant)
For the Redirect URI, make sure to select SPA and then enter the URL where you will be hosting your browZer bootstrapper. For the example used in this documentation, we will use https://entra-demo.ziti.netfoundry.io
For example:
Once all the above fields have been filled in, click the Register button at the bottom of the form.
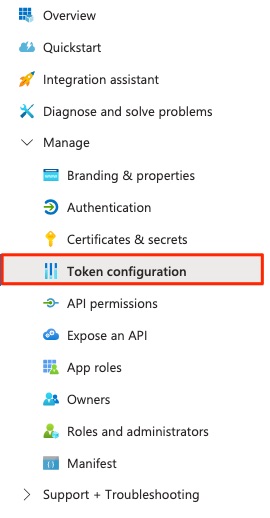
Token configuration
Then click on the "Token configuration" item in the left navbar:
Then click "Add optional claim":
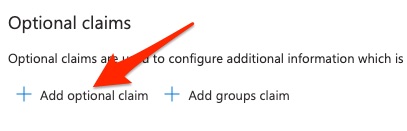
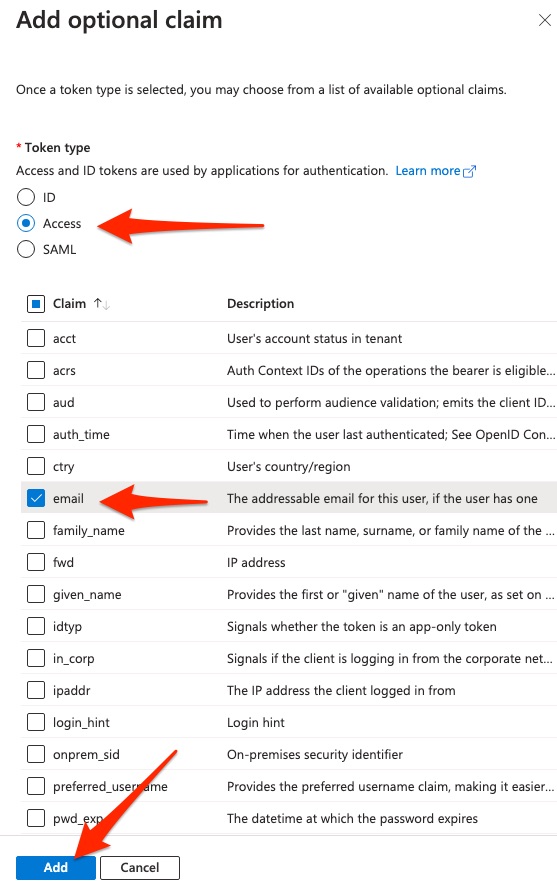
Then select Access as the token type, and select email from the list of claims.
Then click the Add button at the bottom of the form.
For example:
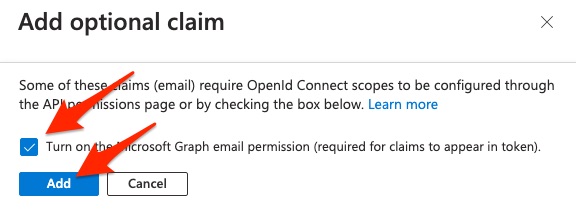
A form will appear. Select the checkbox Microsoft Graph email permission,
Then click the Add button.
For example:
Expose an API
Then click on the "Expose an API" item in the left navbar:
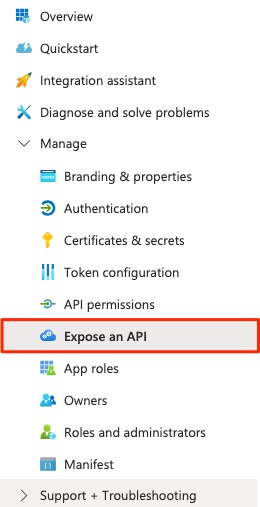
Click Add a scope
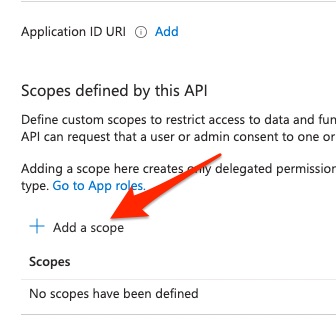
For the Application ID URI, enter the URL where you will be hosting your browZer bootstrapper. For the example used in this documentation, we will use https://entra-demo.ziti.netfoundry.io
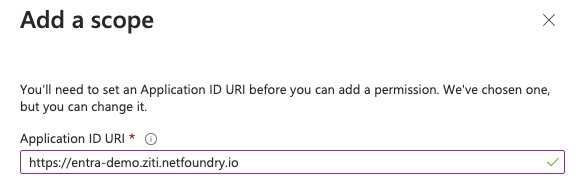
For the Scope name, enter OpenZiti.BrowZer.
For Who can consent, choose Admins and users.
Enter what you like for the descriptions.
Make sure the State is Enabled.
Then click the Add scope button at the borrom of the form.
For example:
Owners
Then click on the "Owners" item in the left navbar:
Add yourself as an owner of the application:
API permissions
Then click on the "API permissions" item in the left navbar:
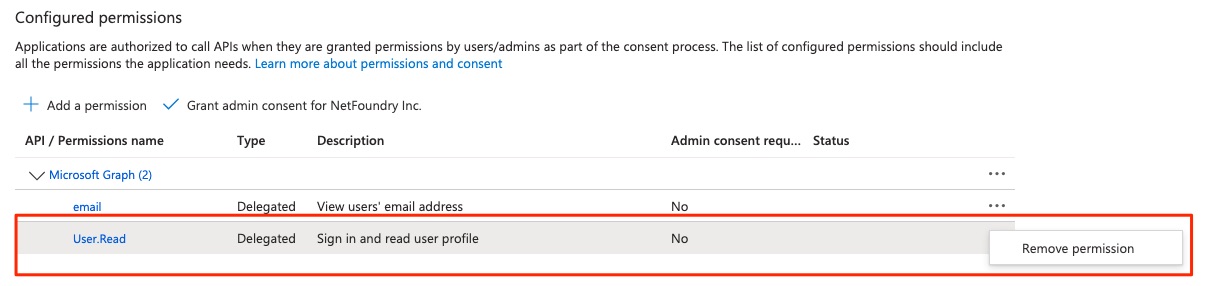
The User.Read permission is not needed for browZer, so you may use the 3-dot menu on the right side to remove it.
Now click Add a permission.
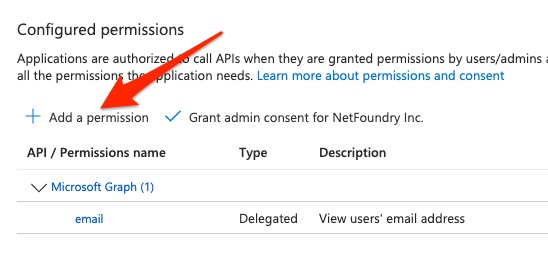
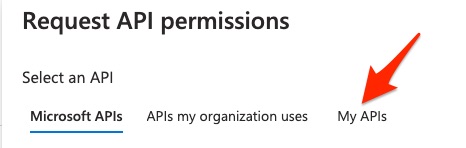
Now click My APIs.
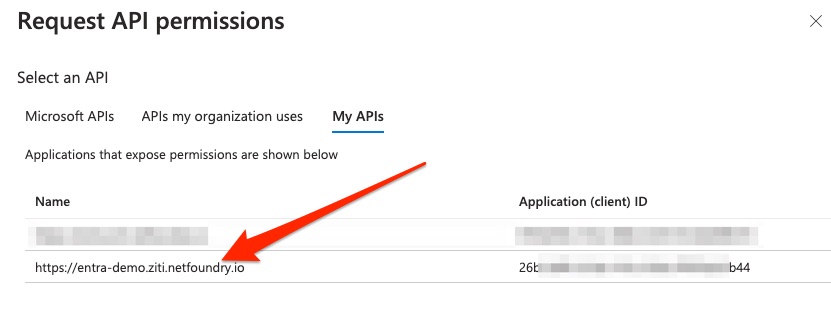
Now click the item representing the URL where you will be hosting your browZer bootstrapper. For the example used in this documentation, we will use https://entra-demo.ziti.netfoundry.io
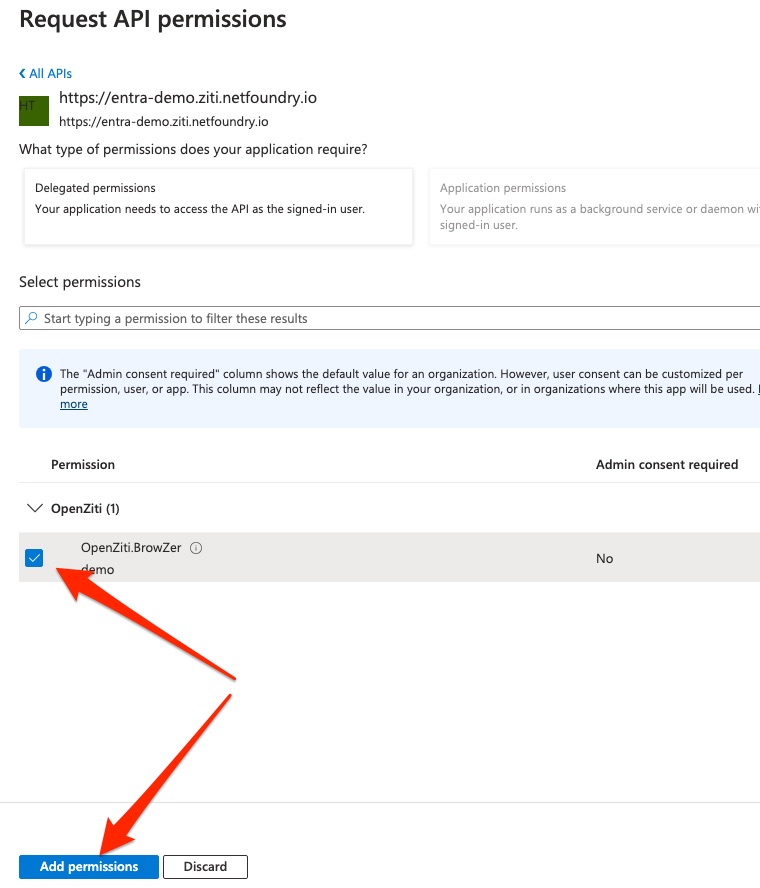
Select the checkbox for OpenZiti.BrowZer, then click the Add permissions button at the bottom of the form.
Manifest
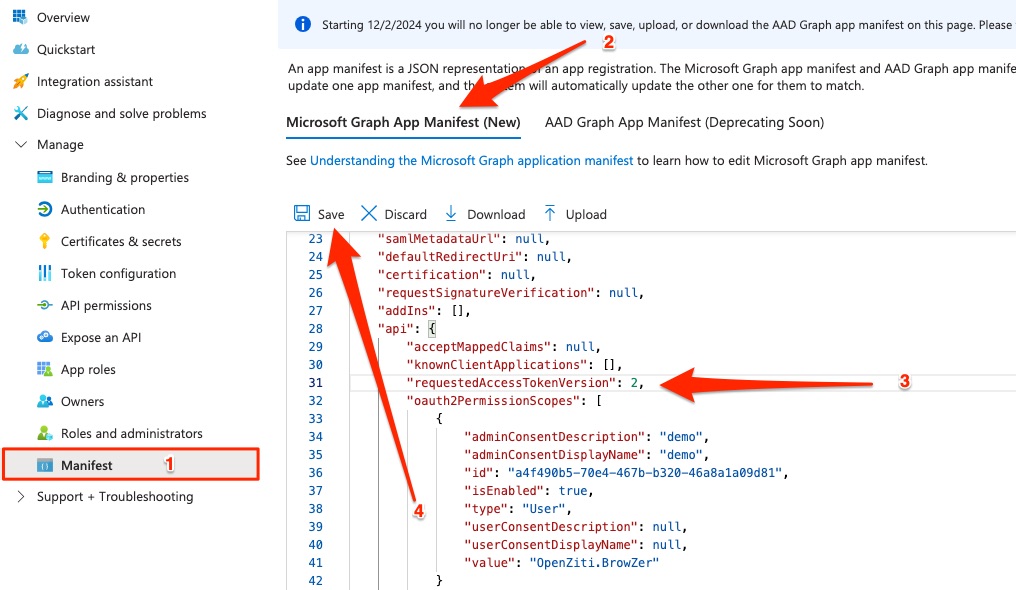
Then click on the "Manifest" item in the left navbar:
Now click Microsoft Graph App Manifest, then scroll the JSON down to line 31 where you see requestedAccessTokenVersion. This field defaults to null.
Change the value to 2. This is extremely important. Failure to complete this step will results in invalid access_token's being produced by Entra during the PKCE process performed between browZer and Entra when a user authenticates.
Then click Save
For example:
Gather IdP Information
Your OpenZiti network must be configured to become aware of your Entra identity provider. OpenZiti refers to the identity provider as an External JWT Signer. Before you can set up the new JWT signer, you must gather some information from the new Entra Application that you just created:
- the
clientId - the
issuer - the
jwks_uri
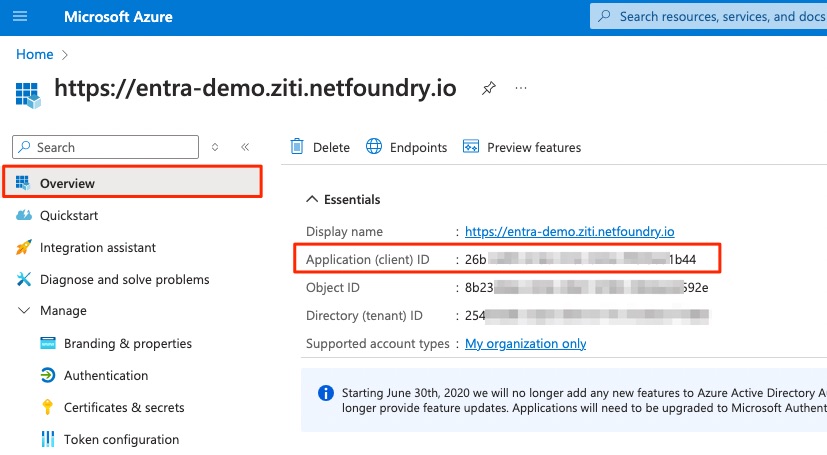
Gather clientId
The clientID value can be found in the Overview tab of the Application you Registered above:
Gather issuer
The issuer can be found via the openid-configuration endpoint that all OIDC-compliant identity providers expose.
The openid-configuration endpoint URL for Entra looks like this:
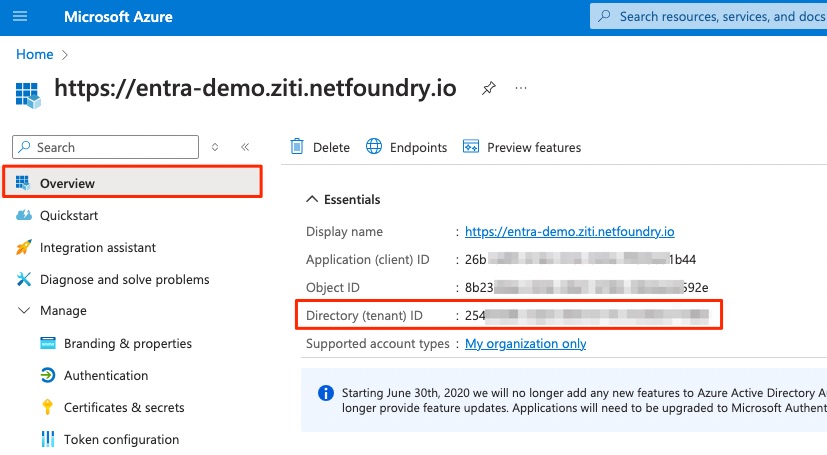
https://login.microsoftonline.com/<YOUR_TENANT_ID>/v2.0/.well-known/openid-configuration
where the value for <YOUR_TENANT_ID> can be found in the Overview tab of the Application you Registered above:
When you enter the openid-configuration endpoint URL (https://login.microsoftonline.com/<YOUR_TENANT_ID>/v2.0/.well-known/openid-configuration) into a browser, you will receive a response resembling the following:
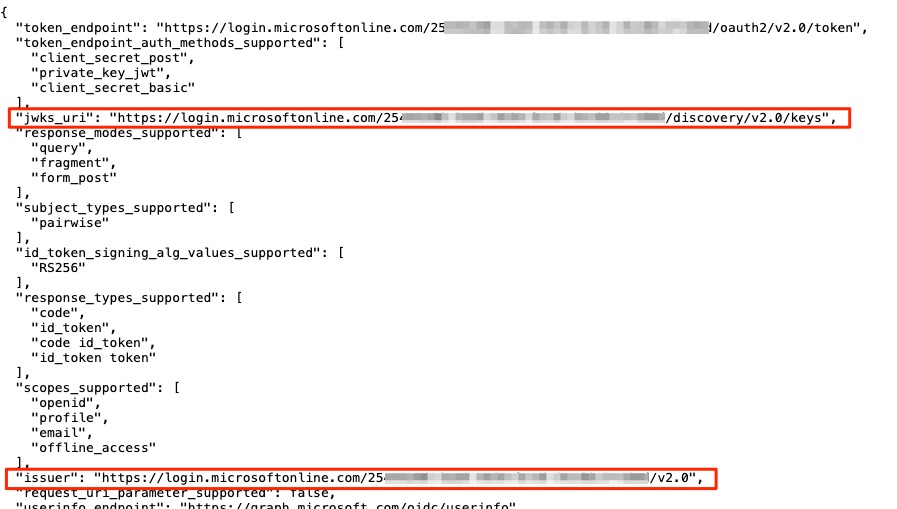
Take note of the issuer value.
Gather jwks_uri
Take note of the jwks_uri value returned from the above openid-configuration endpoint URL.
Create External JWT Signer
Using the values described above, use the ziti CLI to configure an external JWT signer that represents your Auth0 identity provider. You can find details on how to do this in the BrowZer Quickstart documentation